Cool Jobs: The science of secrets
Researchers harness science to encode — and decode — hidden messages

Chick-a-dee-dee-dee. The chickadee gets its name from its distinctive call. The greater the danger, the more “dees” a chickadee adds to the call’s end.
Christopher N. Templeton
By Susan Gaidos
Can you uncover the secret message?
GIFNAFIOYRUMNANTDISOHN RMOATY FBTE AEPNFCEOTDAEOD.
(Stumped? Delete the first letter and then go on and delete every other letter after that.)
It’s not just spies and secret agents who work with codes — many scientists do too. All it requires is an interest in finding repeating patterns, embedded information or surprising solutions to problems.
Scientists have decoded information about the world for centuries. Today, researchers still make and break codes, often in unexpected ways. Here, we profile three actively exploring the world of codes, each in a unique way.
Message in the microbes
Tufts University chemist David Walt is always hunting ways to apply chemistry to solve biological problems. He has developed clever sensors that can probe what turns particular genes on or off. And he has developed tools that can identify individual proteins inside cells, structures way too small to see with ordinary microscopes.

Alonso Nichols/Tufts University
Recently, Walt tackled a different kind of problem. Instead of trying to decode the inner workings of cells, he used cells to encode some secret messages of his own.
The research helps the U.S. military as it seeks new ways for soldiers to transmit information without the enemy knowing. Walt and his colleagues brainstormed a novel idea: Use glowing bacteria to spell out secret messages.
But the common germs they use couldn’t glow without the researchers’ help. For that, Walt’s team relied on a gene that other scientists had discovered back in the 1990s. Present in a species of jellyfish called Aequorea Victoria, this gene allows the animal to glow green-blue.
Walt and his colleagues didn’t harvest the gene. Instead, they ordered it over the Internet from a special supply company. The scientists then used clever techniques to insert the gene into seven different strains of E. coli bacteria. (Unlike the types of E. coli that cause food poisoning, these strains were harmless.) With effort, the scientists engineered each strain of bacteria to glow one of seven different colors, including red, cyan and green, under fluorescent light.

Alonso Nichols/Tufts University
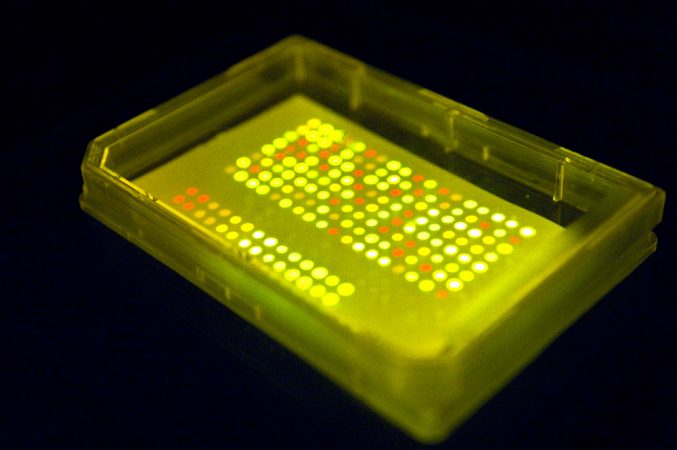
The researchers needed more than seven colors to spell out all 26 letters in the alphabet, the numbers 0 through 9, and various symbols, including ?, ! and @. So the scientists assigned a different two-color combination to each. For example, two side-by-side yellow dots stood for the letter “T.”
To spell out test messages, character by character, Walt’s group placed tiny quantities of their bacteria onto special paper.
Decoding a message first required pressing the paper into a dish of agar; this is a gelatinous substance in which bacteria easily grow. Once these bacteria had grown in number, a fluorescent light revealed the two-color combinations encoded by the germs. Finally, a cipher, or key, helped unlock the message’s meaning.
Walt likens the strategy to using invisible ink, such as lemon juice, on paper. While such secret messages appear within seconds of being held over a light bulb or other heat source, Walt’s bacterial messages take several days to become apparent. That’s because the bacteria need to multiply enough before their fluorescent glow can even be seen.
The scientific team’s code system is slow, but safe. It boasts three different levels of security. First, it is hard to tell if a piece of paper even contains a message written in microscopic bacteria. Second, the messages require a cipher to translate their fluorescent patterns into words, numbers and symbols. Third, the team wrote their messages using bacteria resistant to antibiotics — special medicines developed to target and kill germs. So to read a message, its recipient must first apply an antibiotic to the paper.
Using the wrong antibiotic could wipe out the special bacteria and erase the message. If the recipient used the correct antibiotic, only the message-bearing bacteria would survive and grow. “Any extra bacteria embedded in the message — such as bacterial cells picked up from tabletops — wouldn’t grow because they are sensitive to the antibiotic,” Walt says. “So only the bugs that we want to grow will grow.”
Tests show the system works. While the military hasn’t used glowing bacteria to send any actual messages, they might one day. Meanwhile, Walt is back to cracking biological codes, looking for proteins in the blood that might signal the early presence of developing tumors.
“Dee” is for danger
Biology or saxophone? Chris Templeton didn’t know which to study in college, so he chose both.
A chance stroll through a park convinced Templeton he had made the right choice. During that walk, he heard the expressive notes of a black-capped chickadee. As Templeton listened, he slowly realized the bird sang a different tune each time. “My musical training helped open up my ears to the different sounds that the animals were making,” he says.

Christopher N. Templeton
Curious, the student began focusing on how different species styled their songs. When birds varied their calls, did that indicate they were giving a different meaning to each message?
After receiving college degrees in music and biology, Templeton began graduate school at the University of Montana. There, he began an in-depth study of the sounds animals use to communicate. He focused on chickadee warnings.
When a cat, weasel or other predator threatens a chickadee, the little bird makes a distinctive chick-a-dee-dee-dee. “It’s where the birds get their name,” Templeton explains.
Sometimes, the birds vary their calls. The scientist wanted to find out why. So he decided to show a few scary animals to a captive flock of chickadees. The first animal was stuffed — a small falcon, called a merlin, which preys on chickadees. The small birds responded by first producing lots of calls, then ganging up and attacking the stuffed merlin.
Two weeks later, Templeton showed the fake falcon to the same flock of chickadees. This time, the birds remained calm and silent. They knew the stuffed merlin posed no threat.
Next, Templeton borrowed a few living birds of prey from a bird-rescue organization. One by one, the biologist placed the predators — each leashed and anchored — into the chickadee enclosure. Even though each bird of prey was restrained, its presence again provoked the chickadees. The same thing happened when Templeton introduced other types of predators, including foxes.
As Templeton alternated predators, he realized the chickadees were changing their alarm calls. So Templeton began recording the chickadee tunes. Later, he used a computer to analyze their vocal responses. And it cracked their code.
The computer turned each call into a sonogram, or a wiggly visual representation of the recorded sounds. Each sonogram displayed, second by second, how the chickadee’s pitch rose and fell. The sonograms revealed patterns and variations too subtle even for Templeton’s ears. The changes seemed to reflect the degree of danger each bird had experienced.
“One thing people can hear — and it’s really obvious if you listen to a chickadee — is that they add more ‘dee’ notes to the end of their call for a more dangerous predator,” Templeton says. For example, one chickadee responded to the presence of a small but ferocious pygmy owl by tacking on 23 “dee” notes to the end of its warning call.
Chickadees rely on a repertoire of different vocal signals, about 14 in all. Each contains a lot of information. The birds choose a particular call depending on what they want to communicate, Templeton found.
For predators on land, chickadees use their chick-a-dee-dee-dee call. This summons nearby chickadees to congregate and then to “harass the predator — to drive it out of the area so it can’t sneak up on them later,” Templeton explains. Meanwhile, if a raptor flies overhead, chickadees produce a shrill, high-pitched call. Almost a shriek, this warns other chickadees to dive for cover or freeze in place. Interestingly, other birds pay attention too.
“We know that 50 different species will respond to the chickadee calls,” Templeton says.
Now a research fellow at the University of St. Andrews in Scotland, Templeton recently began studying tropical wrens that sing in pairs. He hopes to figure out how the birds coordinate their duets. Eventually, he may even decode what they are communicating.
“Once you really start listening,” Templeton says, “it’s amazing how clever these birds are, and the variety of useful information they can sing throughout the treetops.”
Criminal codes
By the time millions of people had discovered the world of forensic science through TV programs such as “CSI” and “Forensic Files,” Heather Mahalik was already busy studying blood spatters and collecting hair samples.
She never set out to become a forensic investigator. Instead, the woman had planned on becoming a doctor — patching together patients, not crime scenes. A college classmate convinced her to explore forensics instead.
Back then, in the late 1990s, forensic science still wasn’t the popular subject of TV shows that it is today. If Mahalik was to figure out how forensic experts study blood, gunpowder residues, metals and plastic debris to help solve crimes, she would have to do so on her own. So, like a true scientist, the young woman conducted some research, questioning a real expert — an agent with the Federal Bureau of Investigation.

Heather Mahalik
He described the grisly crime scenes Mahalik might encounter. The agent also explained skills she would need. To Mahalik’s delight, she realized a career in forensics would rely heavily on the math and science she was already studying in preparation for medical school.
By her second year of college, Mahalik switched her major and never looked back. Eventually, she became one of the first four people in the United States to graduate with a degree in forensics and investigative science.
Since then, Mahalik has solved cases involving missing persons, runaways, violent crimes and even terrorism. Today, she decodes digital clues as an expert in cyber crimes for a company in Washington D.C. There, the researcher analyzes information encoded in the hard drives of computers, smartphones and other electronic devices. Her digital sleuthing helps many different law enforcement organizations, from the local police to, yes, the FBI.
Mahalik investigates not only the movement of people, but also of data and computer files too. To do so, she decodes the jumble of digital information concealed in the memory of laptops, smartphones, tablets and other digital devices.
At first glance, this task appears impossible. Any one piece of information — such as a text message or telephone number — might not tell Mahalik much. Combine enough of those information tidbits, however — say, six months’ worth of text messages — and you can put them together in ways that reveal some interesting connections, Mahalik explains.
For example, most cell phones today include a computer chip that bounces radio signals off of satellites that are part of the Global Positioning System, or GPS. This allows the phones to determine their location and then store the information. Mahalik can retrieve these stored data to determine whether a suspect was at the scene of a crime. Other details stored on the phones can reveal much more.
“We can track where a person has been and see whom they have talked to in order to obtain information on their contacts and other targets,” Mahalik explains. Analyzing photos stored on a phone can reveal who took them, as well as where and when.
Digital forensics experts can even retrieve information from devices that their owners tried to remove. That is because deleting a file stored on a hard drive doesn’t really erase it — at least not immediately. Instead, any deleted information remains stored until new data overwrite it.
So, if you have an iPhone with lots of lots of storage capacity — such as 32 gigabytes — supposedly erased information actually stays in your phone “for a very long time,” Mahalik points out.
Widespread use of digital devices has made crime solving much easier than it was even a decade ago, Mahalik says. While she used to travel to crime scenes to gather evidence, now she works out of her own office, cracking the secrets contained inside devices sent her way for analysis.
Secrecy prevents Mahalik from sharing many details about her work. But she admits to putting her scientific background to use every day.
Is her work as a forensic investigator really as exciting as what is portrayed on TV dramas? “It’s not that easy,” Mahalik says, “but I think it’s equally exciting.”
Power Words
agar A gelatinous material made from certain marine algae used as a material (and food source) in which to grow bacteria.
birds of prey Birds, such as falcons and owl, that hunt for their food.
cipher A message written in a secret or disguised way.
cyber A prefix that refers to computers or to a type of system in which computerized or online communication occurs.
digital information The type recorded and stored as a series of ones and zeros.
fluorescent Capable of absorbing and reemitting light.
repertoire A stock of regularly performed songs
forensics The use of science and technology in investigating crimes.
gigabyte A unit of computer memory or data storage capacity equal to one billion bytes. A single byte encodes a single character, such as a letter or digit.
pitch (in music) A property of sound that is determined by its wavelength, such as how high or low it is.
predator An animal that preys on other animals.
protein One of many large and complex organic chemical compounds on which life depends. They form the basis of living cells, muscle and tissues. They are made by linking together chains of smaller building blocks known as amino acids. Among well known stand-alone proteins: the hemoglobin in blood and the antibodies that attempt to fight infections.
raptor A bird of prey.
sonogram An image that represents how a signal varies with time.
strain (as in bacterial) Organisms that belong to the same species that share some small but definable characteristics. For example, biologists breed certain strains of mice that may have a particular susceptibility to disease. Certain bacteria may develop one or more mutations that turn them into a strain that is immune to the ordinarily lethal effect of one or more antibiotics.
vocal Made by the voice.
Word Find (click here to print puzzle)

This is one in a series on careers in science, technology, engineering and mathematics made possible by support from the Northrop Grumman Foundation.